We offer state-of-the-art access control solutions designed to meet these evolving challenges. From card reader systems to cutting-edge biometric technology, our offerings span a range of options that can be customized to fit your business’s unique needs.
Why is Access Control Important?
Security is a multi-layered endeavor, and access control serves as a crucial first line of defense. This is especially important in a world where security breaches are not only becoming more common but also increasingly costly. According to a report by Cybersecurity Ventures, the global damage costs due to cybercrime are expected to reach $6 trillion annually by 2023.
However, it’s not just digital assets that require safeguarding. Physical assets, such as office spaces, warehouses, and other facilities, also need to be protected against unauthorized access. The repercussions of lax access control can be devastating, from theft and vandalism to data breaches and corporate espionage.
Investing in a reliable access control system is thus not an option but a necessity. By selectively restricting and monitoring who can enter your premises or access your digital resources, you can significantly reduce the risk of security incidents and ensure the safety of your assets.
What is Access Control? A Brief Overview
Access control is a security technique that regulates who or what can view, enter, or use resources in a specific environment. It’s an integral part of any comprehensive security plan, encompassing both physical and digital realms. In a physical context, access control might involve systems like gates, locks, and surveillance cameras. Digitally, it refers to measures like firewalls, password protection, and encryption.
There are generally three types of access control:
- Physical Access Control: Focuses on limiting access to buildings, rooms, and physical assets.
- Logical Access Control: Pertains to controlling digital identifiers and limiting access to computer networks, data, and files.
- Hybrid Access Control: A combination of both physical and logical systems, designed to provide comprehensive protection for both types of assets.
While there are various methodologies, from the basic lock-and-key to advanced biometric scans, the ultimate goal is the same: to protect your assets by controlling who has the authority to access them.
Types of Access Control Systems by LogicFortress
When it comes to securing your premises, one size does not fit all. LogicFortress offers a wide range of access control systems designed to meet various security needs and operational complexities. Here’s a rundown of some of their most popular solutions:
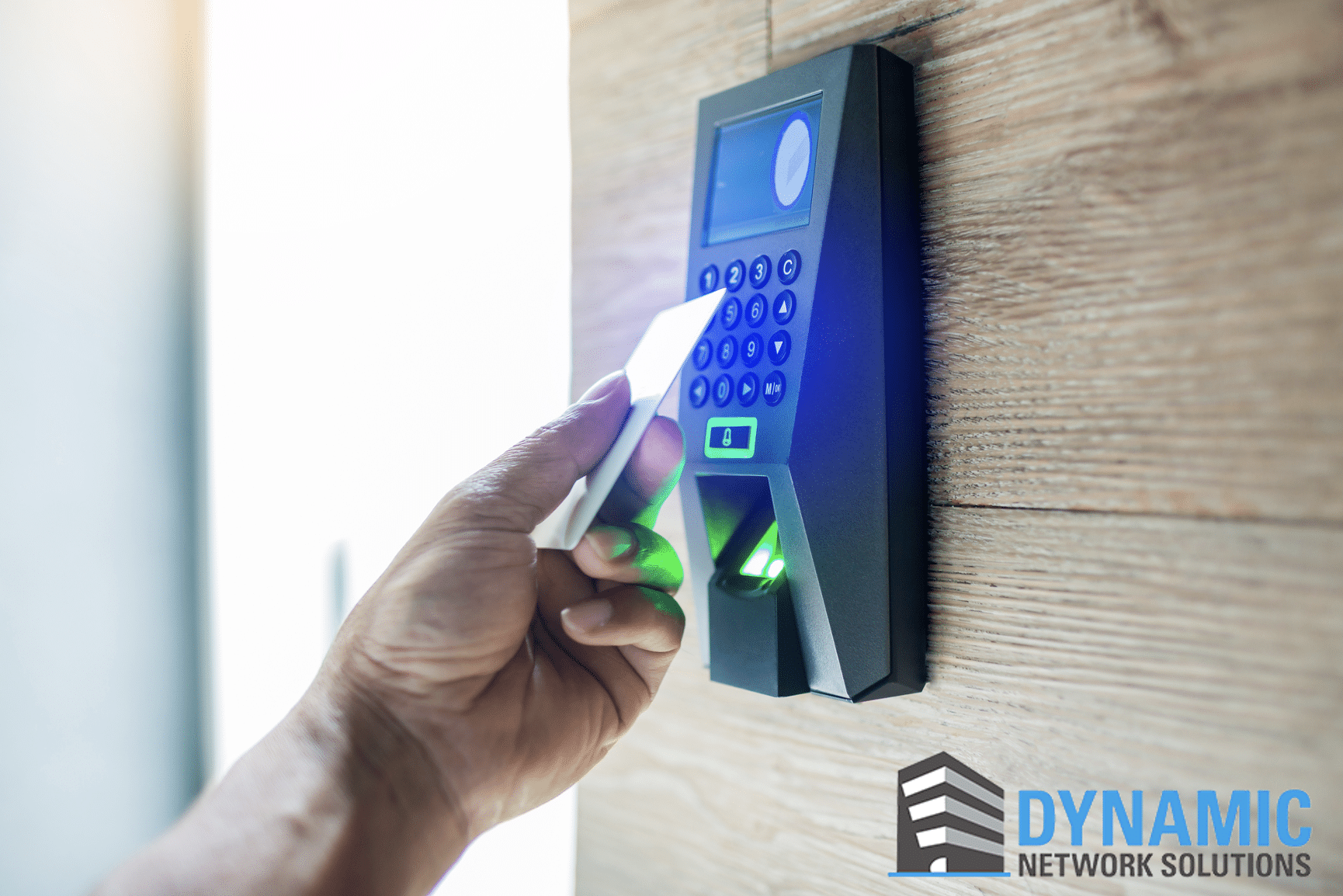
Card Readers
- A classic yet highly effective system, card readers require individuals to swipe or tap a unique card to gain access. Ideal for offices and other professional settings.
Biometric Systems
- Featuring advanced technologies such as fingerprint or retina scans, these systems offer heightened security by authenticating unique biological characteristics.
Mobile Access
- For modern businesses with a digital-first approach, mobile access allows employees to use their smartphones as a key, facilitating easy yet secure access.
Video Intercom
- More than just an audio communication device, video intercoms let you visually verify the identity of anyone requesting entry, making them suitable for high-security areas.
Each of these systems comes with its own set of advantages and can be customized to better fit your specific security requirements. Moreover, LogicFortress’ access control systems can also be integrated with other security features like video surveillance and alarm systems, offering an additional layer of protection.
Benefits of Using Access Control
Increased Security
- With LogicFortress, you don’t just get a lock and key; you get a comprehensive security ecosystem that can deter and detect unauthorized access.
Customizability
- Every business is unique, and so are its security requirements. LogicFortress offers customizable features to match your specific needs, whether it’s restricting access based on roles or time-of-day restrictions.
Scalability
- As your business grows, so does your need for more complex security measures. LogicFortress’ access control systems are designed to scale easily, accommodating more users and broader premises.
Compliance with Security Standards
- In an age where compliance with regulations like GDPR and HIPAA is critical, the advanced features offered by LogicFortress ensure that you meet or exceed all relevant legal requirements.
By offering these benefits, we aim to provide a holistic security solution that not only safeguards your assets but also adds value to your business operations.
Features of Access Control
While the benefits give you a high-level overview, it’s the unique features that set LogicFortress’ access control systems apart from the competition. Here are some standout features you can expect:
Real-time Monitoring
- Gain insights into who is entering or leaving your premises in real-time. This feature is invaluable for quick decision-making in emergency situations.
Integration with Other Security Solutions
- One of the major advantages of choosing LogicFortress is the ability to integrate your access control with other security measures like video surveillance and alarm systems, creating a unified security environment.
User-Friendly Interface
- Simplicity and ease of use are at the core of LogicFortress’ design philosophy. Their systems come with intuitive interfaces, making it easy for authorized personnel to manage and monitor access points.
Advanced Encryption and Security Protocols
- Rest easy knowing that all data flowing through the system is encrypted using the latest security protocols, ensuring maximum protection against cyber threats.
Multi-Factor Authentication
- For areas requiring extra security, multi-factor authentication options are available, requiring two or more verification methods—something you know, something you have, or something you are—to grant access.
By offering these unique features, we ensure that your access control system is not just a security measure but also a tool that simplifies and enhances your operations.
How to Implement LogicFortress’ Access Control
Implementing an access control system isn’t just about installing some hardware and software; it requires thoughtful planning and execution. Here is a step-by-step guide on how to effectively implement LogicFortress’ access control systems in your business:
Planning
- Begin by conducting a security audit to identify the vulnerabilities in your current system and determine the level of security needed.
Installation
- Once you have a plan, the next step is the physical installation of the hardware. This could involve setting up card readers, biometric scanners, or mobile access points at designated areas.
Configuration
- After the hardware is set up, the software needs to be configured. This involves setting up permissions, creating user profiles, and defining security protocols.
Training
- The best security system is only as good as the people using it. Conduct comprehensive training sessions for employees and other stakeholders to ensure they know how to properly use the new system.
Ongoing Maintenance
- Regular software updates, hardware checks, and periodic security audits are essential to ensure that your access control system remains effective and up-to-date.
By following these steps, you ensure that your access control system is not only secure but also optimized for your specific business needs.
Case Studies or Customer Testimonials
Real-world examples offer the most convincing arguments for the efficacy of any product or service. While the names and details have been altered for confidentiality, the following case studies illustrate the effectiveness of LogicFortress’ access control systems:
Case Study 1: A Retail Store Increases Theft Deterrence
- The Challenge: A popular retail store was experiencing high rates of shoplifting and unauthorized access to the inventory room.
- The Solution: LogicFortress implemented a card reader system at the entry points of the inventory room and real-time monitoring in the retail area.
- The Result: Theft rates dropped by 40% in the first three months, and employees reported feeling safer at work.
Case Study 2: A Healthcare Facility Meets Compliance Standards
- The Challenge: A healthcare facility was struggling to meet HIPAA compliance requirements concerning patient data security.
- The Solution: LogicFortress installed biometric systems and multi-factor authentication to secure areas where patient records are stored.
- The Result: The facility successfully passed a surprise HIPAA compliance audit and avoided potential fines.
Case Study 3: A Tech Company Enhances Remote Work Security
- The Challenge: A tech company wanted to ensure secure remote access to their internal systems for their employees working from home.
- The Solution: LogicFortress set up a robust logical access control system with advanced encryption and security protocols.
- The Result: Employees were able to securely access work files remotely, leading to increased productivity and data security.
These case studies demonstrate the versatility and effectiveness of LogicFortress’ access control systems in solving real-world security challenges.
Final Thoughts and Next Steps
 In an increasingly interconnected world, the importance of robust access control systems cannot be overstated. Whether it’s protecting your physical assets or securing digital information, Dynamic Network Solutions offers a range of solutions designed to meet the unique security requirements of various industries. From traditional card readers to advanced biometric systems, their offerings are both comprehensive and customizable.
In an increasingly interconnected world, the importance of robust access control systems cannot be overstated. Whether it’s protecting your physical assets or securing digital information, Dynamic Network Solutions offers a range of solutions designed to meet the unique security requirements of various industries. From traditional card readers to advanced biometric systems, their offerings are both comprehensive and customizable.
Next Steps:
- Assess Your Needs: Before you can implement an effective access control system, you need to know what you’re protecting and why. Perform a security audit to identify vulnerabilities and determine the level of security required.
- Consult the Experts: Reach out to LogicFortress for a consultation. Their team of experts will guide you in choosing the right access control system that aligns with your needs and budget.
- Implementation and Training: Once you’ve selected a system, the next steps include installation, configuration, and training. Ensure that all stakeholders are familiar with how to use the new system effectively.
- Stay Updated: Security threats are ever-evolving. Keep your systems updated and conduct regular security audits to ensure that your access control measures are always one step ahead of potential threats.
By taking these steps, you can significantly enhance the security of your business and ensure that your assets—both physical and digital—are well-protected.




