Optimizing New England’s Largest Food Distributor
 Who: New England’s Largest Food Distributor
Who: New England’s Largest Food Distributor
What: Optimizing WiFi & Surveillance System for New England’s Largest Food Distributor
Why: Fiber Optic was in place, but WiFi could not keep up with the demands of the company’s mobile phones, tablets, and inventory scanners.
How was this resolved?
- Network Security: Ubiquiti Security Gateway
- Wired Network Access: Managed 48 Port POE Switches
- Wireless Network Access: 18 Ubiquiti Access Points
- Cameras: Over 50 Ultra-High Definition Cameras
- Net Savings: Incalculable
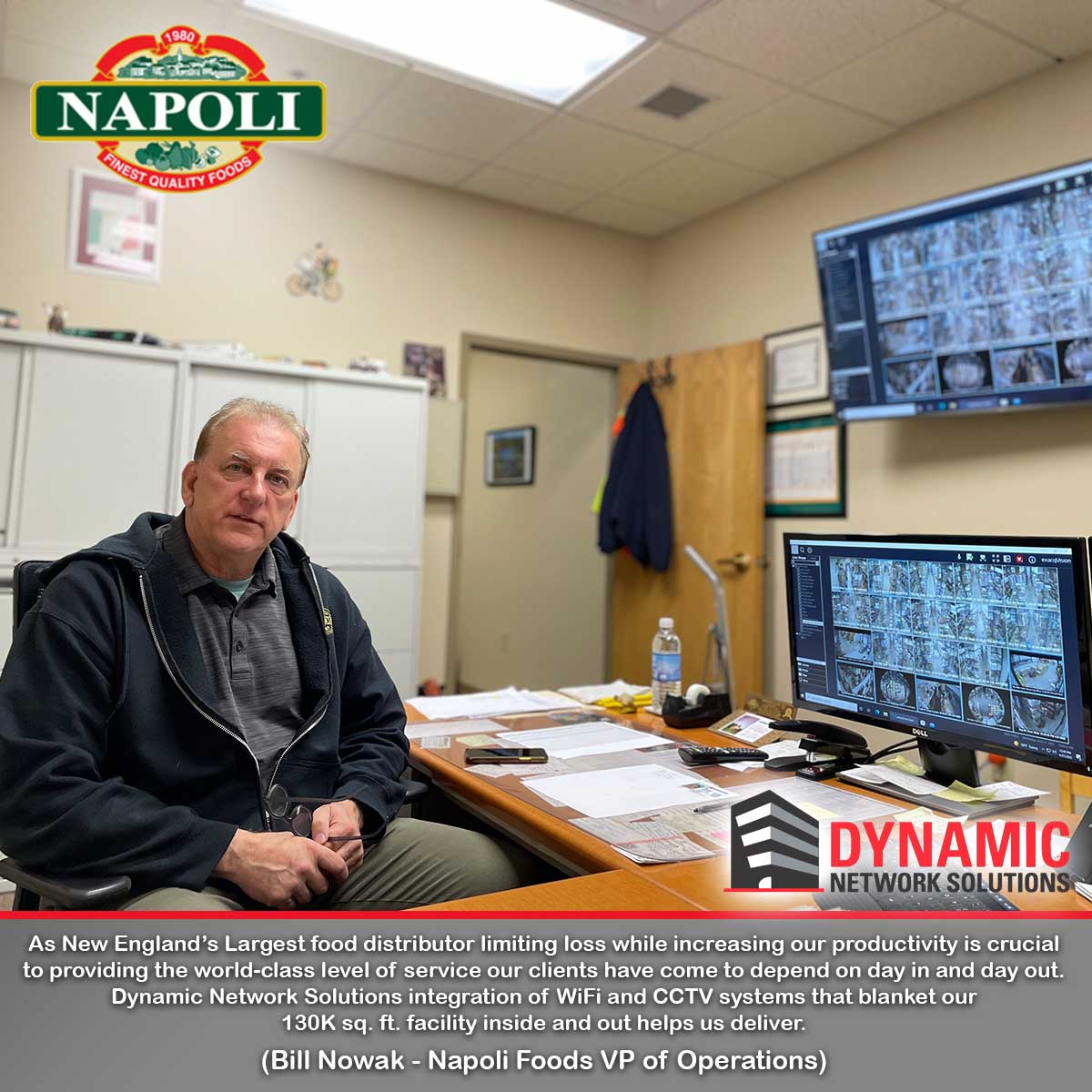
Napoli Foods came to DNS with an antiquated Rukus wireless mesh system that frequently left them without adequate WiFi coverage and a Panasonic CCTV system that was at best intermittent. Aside from the challenges Napoli faced with the cameras themselves, the system was loaded with blind spots in key areas throughout their 130K square foot facility.
With long-range access points inside and out they now have consistent WiFi in every corner of their office, warehouse, and shipping yard. Along with seamless WiFi coverage, the 50+ HD and UHD Hikvision cameras DNS deployed inside and out gave management the tools they needed to limit any potential loss and enhance productivity throughout their operation, better enabling them to maintain their place as New England’s top food distributor.
With smart hardware configuration and cost-efficient software, this client was able to save substantially over potential alternative solutions, because they planned and carried out their IT system integration with LogicFortress. Quite often, the investment is not in up-front costs, but in the hidden licensing fees for hardware & software. In this particular case, the savings came from STARTING WITH systems free of recurring vendor fees and PRESERVING THE RIGHT to upgrade.
At DNS we continually test the software and hardware products hitting the market to find the few quality vendors that enable the greatest flexibility for the most economical price.
If you would like more information on how to place a buffer between you and your hardware licensing costs while improving operational efficiency, simply fill out our contact page.